Data Assurance
turning data from a liability to an asset
gaining value from big data
with millions of transactional data from multiple systems, it is a challenge to have all the data tied together to feed analytics.
- data is missing
- data is wrong (duplicates/contradicting)
- different file formats
- different data syntax
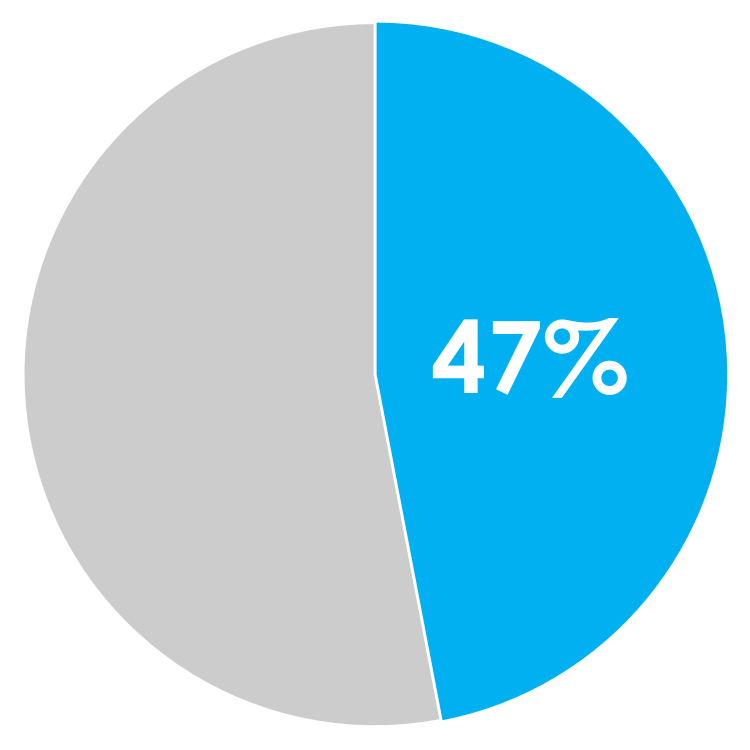
of the time data is late without data governance
source: Aberdeen Group, 2012

organized for indisputable insights
Competitive Insights ensures the
consistent processing of the native data
from all of the transactional system sources.
Competitive Insights' solutions
have a robust data assurance methodology,
a critical requirement to the reliability
of an effective analytical solution.
data governance - critical to realizing profit performance white paper>
Third-Party Expertise & Oversight

- Experienced with over 20 years of projects across multiple industries
- Expertise in providing innovative solutions quickly and efficiently
- Personal to addressing the needs and supporting success of clients
- Using Artificial Intelligence (AI) for autonomous data validation
more on Competitive Insights' experience>

Cross-Functional Agreement by Customer
- Customized data processing rules
- Validated by Subject Matter Experts
- Unquestionable insights on financial performance
blog: Global Analytics and Big Data Survey>
Data Governance
Machine Learning (ML) and Artificial Intelligence (AI) automated and quick processes minimizing IT involvement include:
- Data Identification
- Data Transmission
- Data Receipt
- Data Storage & Management
- Data Checking
- Data Linking
- Data Processing
- Data Transformation
- Data Validation
- Data Quality Assurance
blog: don't use data integrity issues as a crutch>


Best-in-Class System Access & Security
- Compliant to SAS70 Type II standard as highest level of security
- Security with double authentication access
- Tailored system for business user’s needs